How to Allow a Non-Admin user to manage a specific Service using SC.EXE with Least Privilege Manager
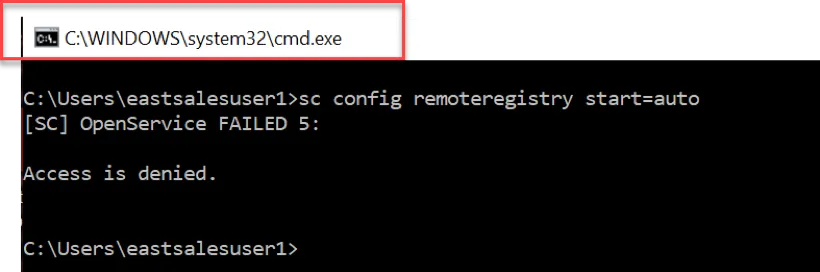
The steps in the example below will allow a Non-Admin user to manage the Remote Registry service using the SC.EXE command. Before you start, you can pre-test that a standard user cannot use the command line to start the service.
Follow the steps to start the service using the command line.
Step 1 – Use command sc config remoteregistry start=auto to start your test.
Step 2 – Create an LPM Combo rule using Path and Command line.
Step 3 – For the Path, use: C:\Windows\System32\sc.exe
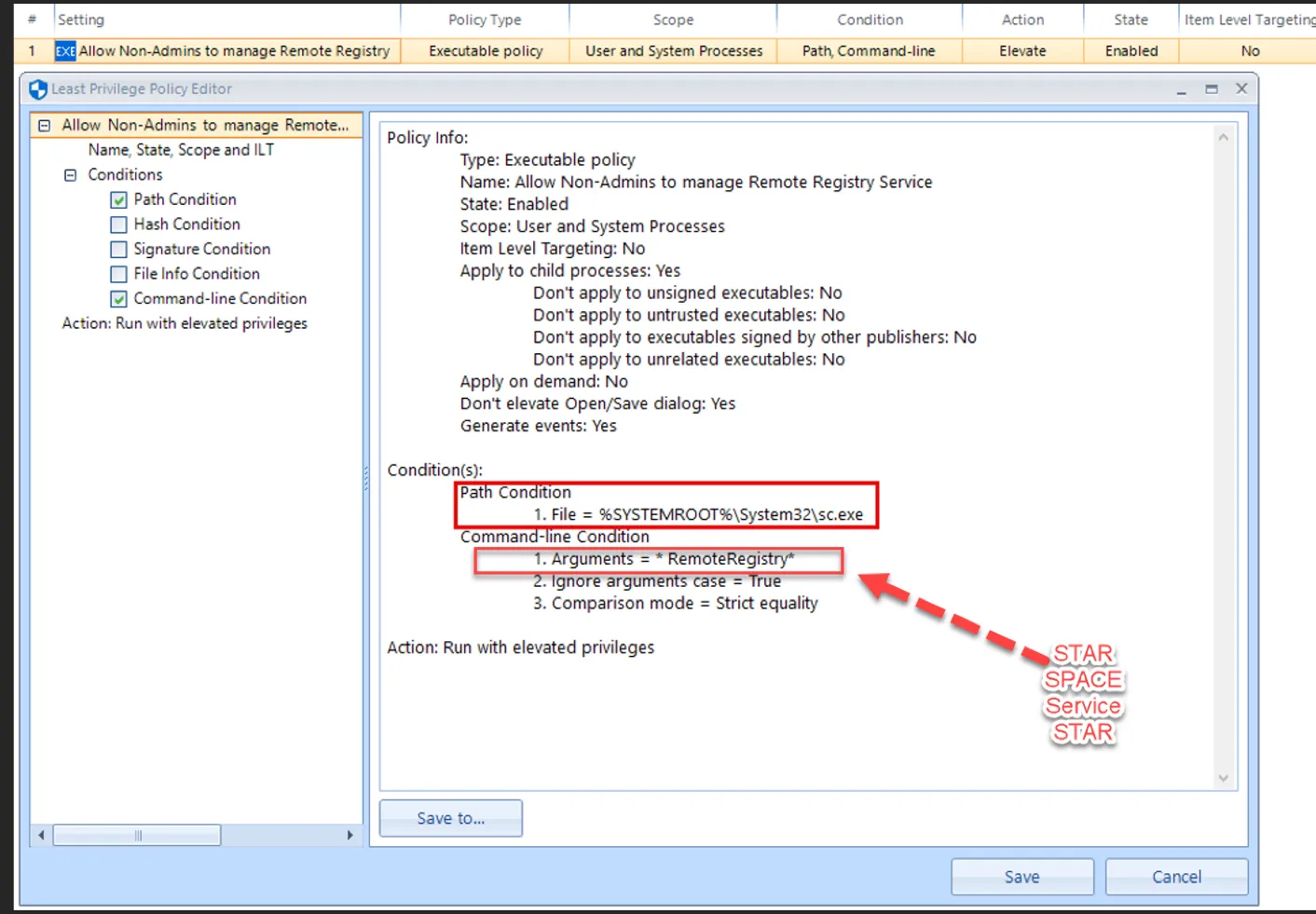
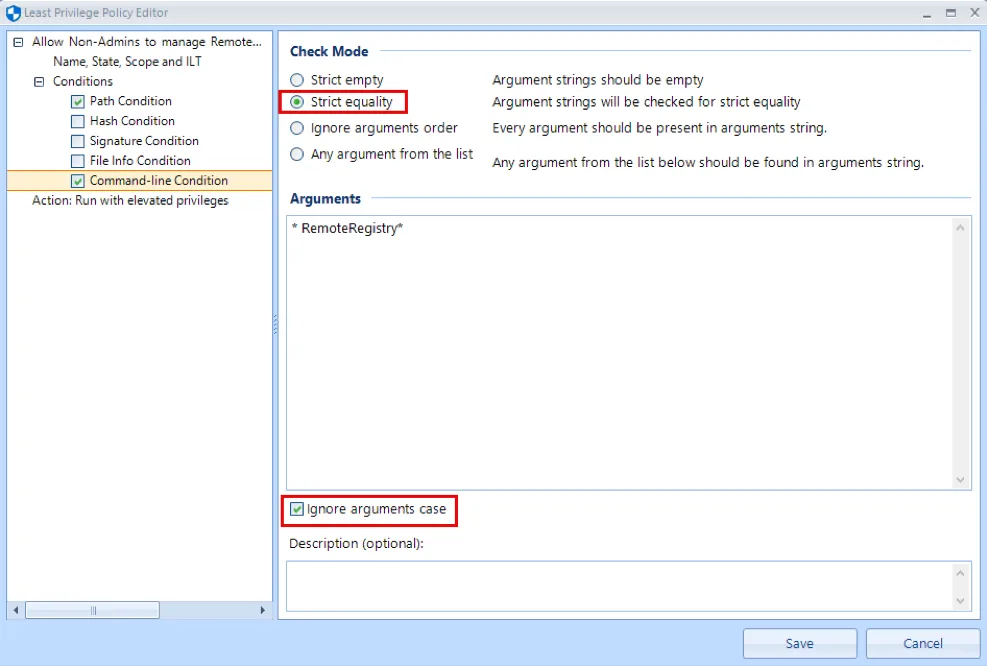
Step 4 – For the Command line use the syntax: <ServiceName> (*space<ServiceName>*). For
example:RemoteRegistry. Ensure that both Strict equality and Ignore arguments case options
are checked.
NOTE: You can use services.msc and look at the properties of an individual service to get the
ServiceName, or you can use the sc query command from CMD to get the ServiceName.
Step 5 – Apply the policy to the user(s) or computer(s) that need to receive the policy.
Step 6 – Test from a CMD prompt as a standard non-admin user to see if you can manage the Remote
Registry service using the SC.EXE command. SC Config RemoteRegistry Start=Auto
NOTE: Since the Remote Registry service is disabled by default we need to enable the service and choose its startup type.
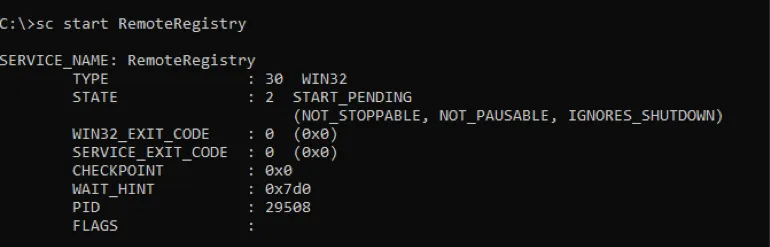
Step 7 – Start the service using the following command: SC Start RemoteRegistry.
Step 8 – Stop the service with the following command: SC Stop RemoteRegistry.
Step 9 – Disable the service with the following command:
SC Config RemoteRegistry Start=Disabled.
You can use the XML policy below as an example.
[Copy](javascript:void(0);)
XML Policy
<?xml version="1.0" encoding="utf-8"?>
<policy xmlns:lpm="http://www.endpointpolicymanager.com/2016/LPM/CommonTypes" xmlns:ext="http://www.endpointpolicymanager.com/2019/LPM/PolicyEntryExtension" xmlns:security="http://www.endpointpolicymanager.com/2016/LPM/Security" xmlns:pd="http://www.endpointpolicymanager.com/2014/Policies/PolicyData" xmlns:pp="http://www.endpointpolicymanager.com/2014/CommonTypes" id="{08556a99-a6ea-4ce9-9dee-9cc490567c39}" productId="{58DE0268-6384-49E0-A333-20EC46654B82}" scope="machine" timestamp="1709820468" xmlns="http://www.endpointpolicymanager.com/2016/LPM/PolicyData">
<collection order="0" id="{68b6fd6b-2d0c-4fa7-b7f8-4a74fd67d909}" displayName="Container for policy: Allow Non-Admins to manage Remote Registry Service Using SC.EXE">
<entry order="0" scope="machine" id="{4943c522-8613-438f-b7b5-eb0c25032787}" displayName="Allow Non-Admins to manage Remote Registry Service Using SC.EXE">
<rule-v1>
<executableRule xmlns="http://www.endpointpolicymanager.com/2016/LPM/Rules-V1">
<conditions xmlns="http://www.endpointpolicymanager.com/2016/LPM/ExecutableRule">
<pathCondition xmlns="http://www.endpointpolicymanager.com/2016/LPM/Rules">
<path kind="File">%SYSTEMROOT%\System32\sc.exe</path>
</pathCondition>
<commandLineCondition xmlns="http://www.endpointpolicymanager.com/2016/LPM/Rules">
<value>* RemoteRegistry*</value>
<useAndSpecifierForArguments>false</useAndSpecifierForArguments>
</commandLineCondition>
</conditions>
<settings justificationTextRequired="false" restrictOpenSaveDialog="true" xmlns="http://www.endpointpolicymanager.com/2016/LPM/ExecutableRule">
<applyToChildProcesses>true</applyToChildProcesses>
</settings>
<action xmlns="http://www.endpointpolicymanager.com/2016/LPM/ExecutableRule">
<changeProcess xmlns="http://www.endpointpolicymanager.com/2016/LPM/Actions">
<security:changeToken baseToken="Elevated">
<security:groups />
<security:privileges />
</security:changeToken>
</changeProcess>
</action>
</executableRule>
</rule-v1>
</entry>
</collection>
</policy>