SG_SecurityAssessment Job
The SG_SecurityAssessment job performs checks against Windows security best practices in order to proactively identify critical security configurations that leave the environment vulnerable to attack. The result is a report which provides a listing of findings by severity and category with corresponding details that can be used to prioritize and remediate security issues.
Recommended Configurations for the SG_SecurityAssessment Job
Dependencies
One or more of the following jobs must be run to generate data for the report:
-
Authentication
- SG_LSASettings
- SG_SecuritySupportProviders
- SG_WDigestSettings
-
Open Access > SG_OpenFolders
-
Privileged Accounts
-
Local Administrators
- SG_LocalAdmins
- SG_MicrosoftLAPS
-
Logon Rights
- SG_AccountPrivileges
- SG_LocalPolicies
-
Service Accounts > SG_ServiceAccounts
-
-
Security Utilities > SG_PowerShellCommands
Targeted Hosts
None
Schedule Frequency
This job can be scheduled to run as desired.
Workflow
Step 1 – Run one or more of the jobs needed to generate data for this report.
Step 2 – Schedule the SG_SecurityAssessment job to run as desired.
Step 3 – Review the report generated by the job.
Analysis Tasks for the SG_SecurityAssessment Job
Navigate to the Windows > SG_SecurityAssessment > Configure node and select Analysis to view the analysis tasks.
CAUTION: Do not modify or deselect the selected analysis task. The analysis task is preconfigured for this job.
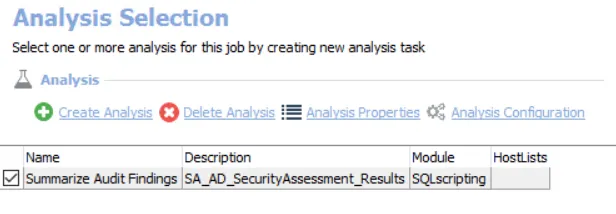
The default analysis task is:
- Summarize Audit Findings – Creates the SG_SecurityAssessment_Results table accessible under the job’s Results node
In addition to the tables and views created by the analysis tasks, the SG_SecurityAssessment job produces the following pre-configured report.
| Report | Description | Default Tags | Report Elements |
|---|---|---|---|
| Systems Security Assessment | This report summarizes security related results from the Windows solution set. | GDPR, SOX, PCI, HIPAA | This report is comprised of four elements: - Pie Chart – Displays a findings by severity - Table – Provides scope of audit details - Table – Displays details on security assessment results - Table – Provides details on findings by category |